WooCommerce has become one of the most popular eCommerce platforms in the world, powering millions of online stores. With that level of adoption, however, comes increased attention from cybercriminals looking to exploit store owners’ trust, especially when it comes to urgent matters like website security.
In April 2025, a particularly deceptive phishing campaign began circulating, preying on WooCommerce users with emails disguised as official security alerts. These messages warn of a “critical vulnerability” affecting the store and urge the recipient to download a security patch. But instead of fixing any issues, the download installs malicious code designed to hijack the site, create hidden admin users, and exfiltrate customer data.
The sophistication of this scam has alarmed both users and cybersecurity experts alike. In one reported case, a WooCommerce store owner shared their experience after receiving one of these emails—highlighting just how convincing the fake message was and how easily it could have led to disaster.
I just received a phishing email (see image). It looked suspicious, coming from mail-woocommerce.com. I followed the link on a virtual machine, and the page looks almost authentic. They even have fake reviews. I downloaded the proposed ‘patch’, and it’s clearly malicious, with cryptic code. It creates one or more admin users, fetching data from somewhere. The funny thing is that the domain from which they serve the patch is almost identical to woocommerce.com, it’s ‘woocommerċe.com’ with the tiny diacritic on the last ‘c’. On a black on white screen, it could be overlooked as a speck of dust. That is clever, in twisted, wicked way
To stay protected against threats like this, it’s essential to stay informed and secure your site properly. Guide to WooCommerce security outlines additional ways to prevent fraud and safeguard your online business.
How the WooCommerce Phishing Scam Unfolds: Step-by-Step Breakdown of the Attack Targeting Store Owners
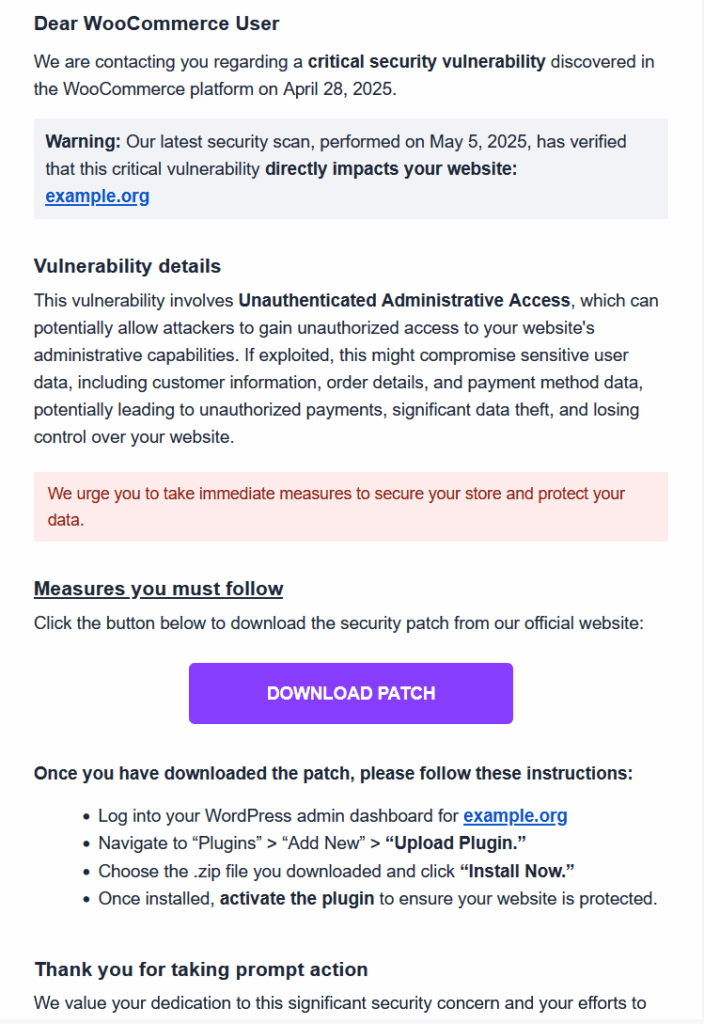
The phishing campaign operates through a calculated, multi-step approach designed to trick even tech-savvy users:
1. Deceptive Email Messaging
Victims receive fake emails from addresses like help@security-woocommerce.com, incident@notify-woocommerce.com, or help@support-woocommerce.com. These messages claim to be urgent notices about a critical security flaw and often include the store’s actual URL to enhance credibility. The language is carefully crafted to sound official and alarming, pushing the recipient to act quickly.
2. Homograph Attacks (Punycode Spoofing)
A notable tactic used in this campaign is IDN spoofing, or homograph attacks. For example, attackers registered domains like https://xn--woocommere-7ib.com, which visually render as woocommerċe.com in many browsers. The character “ċ” (with a dot below) closely resembles a standard “c,” making the domain appear genuine at first glance—especially when skimmed quickly.
3. Fake Patch Installation
The email urges users to download and install a file labeled as a “critical WooCommerce patch.” The file typically mimics legitimate naming conventions (e.g., woocommerce-security-patch.zip) and appears trustworthy. However, once uploaded and activated in WordPress, the file:
- Executes hidden malicious code
- Creates stealthy admin users with names like
wp-supportoradmin-help - Establishes long-term backdoors for ongoing access
- Sends sensitive store data to external command-and-control servers
4. Professional-Level Deception
These phishing websites are meticulously designed to mirror the official WooCommerce interface. They include fake customer reviews, branded graphics, and familiar UI elements to reduce suspicion. Everything—from the download button to the footer—aims to trick store owners into believing the site is authentic.
This campaign illustrates just how advanced and dangerous modern phishing tactics have become. Store owners must remain vigilant and never install updates or plugins from unsolicited emails or third-party domains.
How to Recognize Phishing Emails Targeting WooCommerce Stores
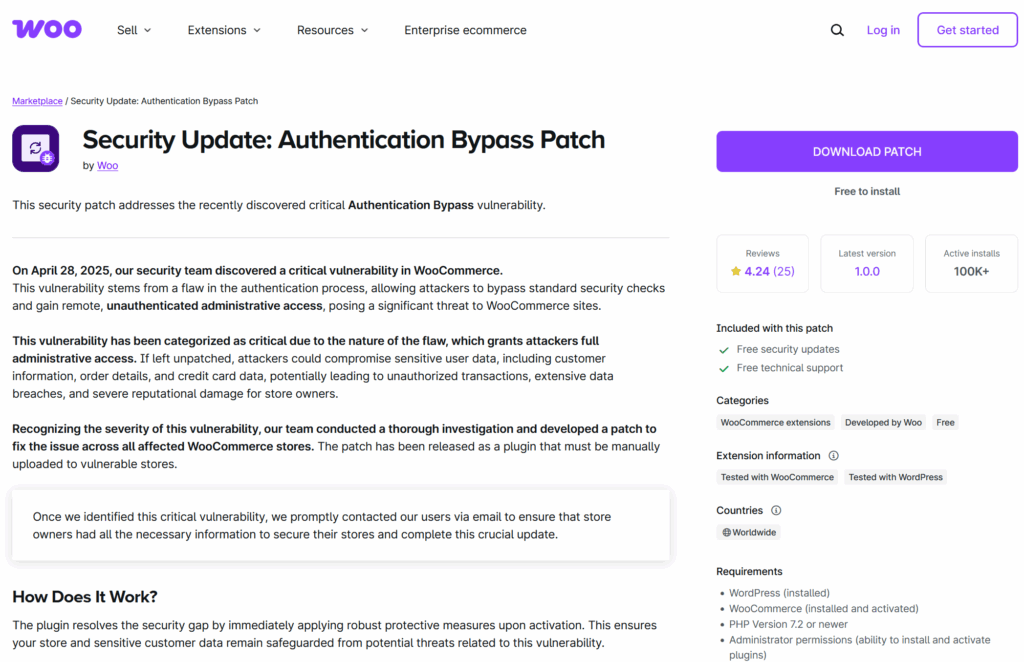
Phishing emails targeting WooCommerce merchants are crafted to look like urgent security alerts, but they often contain subtle — and sometimes not-so-subtle — red flags. Here’s how you can tell if that WooCommerce email in your inbox is actually a scam:
1. Unofficial or Suspicious Email Addresses
One of the first signs of a phishing email is a sender address that looks vaguely official but isn’t. These emails often come from domains that impersonate WooCommerce or Automattic. Common fraudulent email addresses include:
help@security-woocommerce.comincident@notify-woocommerce.comhelp@support-woocommerce.com
They may contain “woocommerce” in the name, but they are not affiliated with WooCommerce. Always verify that the email is coming from an authentic domain such as @woocommerce.com or @automattic.com.
2. Tricky URLs Using Punycode or Lookalike Characters
These phishing attempts often include links that use Punycode, a way to disguise foreign characters in URLs. A malicious domain like:
https://xn--woocommere-7ib.com
May display in your browser as:
woocommerċe.com
At a glance, the difference between “c” and “ċ” can be nearly invisible — especially on mobile devices or smaller screens. This trick, known as a homograph attack, is designed to deceive users into thinking they’re on a legitimate WooCommerce site.
3. Alarming Claims About Site Vulnerabilities
Scammers try to create urgency by claiming your site has been exposed to a critical security vulnerability. These messages often:
- Reference your actual store domain
- Include fake disclosure dates like “April 14, 2025”
- Demand immediate action to avoid data loss or legal consequences
This scare tactic is meant to override your caution and get you to click without verifying the legitimacy of the message.
4. Malicious “Security Patch” Files
Many phishing emails contain a downloadable file or link labeled as a “WooCommerce security patch” or urgent update. While it may look like a plugin or update file, it is actually malware.
Once downloaded and installed, these fake patches can:
- Create hidden WordPress admin accounts
- Open backdoors into your site
- Steal customer data or payment details
- Corrupt your database or install persistent scripts
The Hidden Dangers Behind the “Download Patch” Button: WooCommerce Phishing in Action
Clicking on a fake “Download Patch” button in a phishing email might seem like a minor mistake — but it can unleash a serious security breach on your WooCommerce store. These fraudulent updates often come in the form of files named woocommerce-security-patch.zip, designed to look official and trustworthy. But behind the scenes, they hide a complex chain of cyberattacks.
Here’s what really happens once the file is installed:
Step 1: Silent Malware Deployment
After the fake plugin is uploaded and activated in your WordPress dashboard, it immediately executes encrypted or obfuscated code in the background. This allows it to slip past basic security checks and integrate directly into your core files or database.
Step 2: Stealth Creation of Admin Accounts
The malware’s first strategic move is to create unauthorized admin users. These backdoor accounts often have names like wp-support, admin-helper, or slightly altered versions of legitimate usernames to avoid drawing attention.
These hidden accounts give attackers persistent access — even if you remove the malware itself.
Step 3: Backdoor Installation
Next, the malware installs one or more backdoors — often disguised as plugin files, theme template modifications, or WordPress cron jobs. These allow attackers to access your site remotely at any time, even after visible traces of the hack have been removed.
Unless you conduct a deep file scan, these backdoors can remain hidden indefinitely.
Step 4: Data Theft in the Backgroun
With access secured, the malware starts exfiltrating sensitive data. This may include:
- Customer names and emails
- Order history
- Admin login credentials
- Payment and billing information
All of this is sent to an external command-and-control server, potentially violating data privacy laws like GDPR and seriously damaging customer trust.
To mitigate these risks, it’s crucial to Effectively Use the Blacklister Plugin to Protect Your WooCommerce Store from Fraud, developed by Aelia. This powerful tool helps block access from suspicious IPs, bots, and malicious actors—before they can compromise your store.
How to Spot Fake WooCommerce Emails
It’s important to know that WooCommerce will never send plugin files, updates, or security patches as email attachments or direct download links from unofficial third-party domains.
Official WooCommerce security communications will always:
- Originate from an @woocommerce.com or @automattic.com email address.
- Direct you to trusted websites like WooCommerce.com or WordPress.org for downloads and information.
- Provide thorough documentation, clear verification steps, and transparent instructions.
If an email doesn’t follow these guidelines, treat it as suspicious and don’t trust it.
What to Do If You Receive a Phishing Email
If you suspect an email is fraudulent, avoid engaging with it. Instead, follow these steps:
1. Do Not Click Any Links
Avoid clicking any links, even if they look safe. Phishing emails often hide malicious URLs behind seemingly harmless buttons or text. Clicking could redirect you to dangerous sites or trigger malware downloads.
2. Do Not Download or Open Attachments
Never download or install files from emails unless you are absolutely certain about the sender. These files, disguised as “patches” or “updates,” often contain malicious code that can:
- Install malware or spyware on your site
- Create unauthorized admin accounts
- Modify your website’s code to open hidden backdoors
If you’ve already downloaded the file, do not open or run it.
3. Report the Email as Phishing
Use your email provider’s “Report phishing” feature—available in platforms like Gmail and Outlook—to flag the email. You can also report suspicious domains to your hosting provider or WooCommerce support. This helps prevent others from falling victim to similar scams.
Secure Your WooCommerce Store: Tips to Avoid Phishing and Fraud
Keeping your WooCommerce store secure is vital, especially with ongoing phishing attacks targeting store owners. Here are some proactive steps to protect your business and customers:
1. Only Install Updates from Trusted Sources
Make sure all WooCommerce core, plugin, and theme updates come directly through your WordPress dashboard or from WooCommerce.com. Avoid installing files from email attachments or unknown third-party sites—even if the email looks legitimate.
2. Enable Automatic Updates for Security Patches
WooCommerce and reputable plugin developers frequently release security patches. Enabling auto-updates ensures your store stays protected without manual effort, minimizing the risk of exploitation.
3. Use Strong Passwords and Two-Factor Authentication
Protect your admin accounts with strong, unique passwords and enable two-factor authentication (2FA). This adds an essential extra layer of security against unauthorized logins.
4. Install Plugins Only from Verified Sources
Download and install plugins exclusively from trusted platforms like WooCommerce.com or WordPress.org. Plugins from unverified sources might contain harmful code or backdoors.
5. Block Suspicious Activity Using the Aelia Blacklister Plugin
For an extra layer of defense, consider using the Aelia Blacklister plugin for WooCommerce. This tool allows you to automatically block orders from suspicious users based on customizable criteria, such as:
- Customer name or address
- Email or phone number
- IP addresses or IP ranges
If a match is found, the plugin stops the checkout and shows a tailored message, helping prevent repeated fraud attempts or dangerous traffic from affecting your store.
